

A new checkout flow looks flawless to the product team. Weeks of development, rigorous QA testing, stakeholder sign-off. Then a security tester approaches it like an attacker would-chaining together small cracks that nobody else noticed-and demonstrates how customer payment data could be extracted in minutes.
This is web penetration testing in action.

According to the IBM Cost of a Data Breach Report 2025, the global average cost of a data breach now stands at $4.44 million. In the United States, that figure rises to over $10 million. Web application vulnerabilities remain a primary attack vector-responsible for roughly a quarter of all confirmed breaches globally.
Yet the majority of these attacks exploit weaknesses that could have been found and fixed before attackers got there first.
What Is Web Penetration Testing?
Web penetration testing-sometimes called a web pen test or web application pen test-is a structured, time-bounded security assessment where specialists attempt to compromise your web applications and related components. The goal is to reveal how a real adversary could gain access, use that access, and persist within your systems-then explain exactly how to stop it.
Think of it as a fire drill for your digital systems. Security professionals simulate real attacks to discover where your defences are weak, then provide prioritised recommendations you can act on immediately.
For methodology baselines, reputable testers follow frameworks like the OWASP Web Security Testing Guide and NIST SP 800-115. These provide structured approaches that ensure comprehensive coverage rather than ad-hoc testing.
More Than Just a Checklist
A modern web application pen testing engagement maps your entire attack surface. That includes APIs, microservices, authentication flows, third-party integrations, single sign-on, mobile clients, and the cloud infrastructure that supports your application.
Unlike a checklist audit, web application penetration testing adapts as it learns. Testers follow leads, change tactics, and chain weaknesses together to demonstrate practical impact. The unique abilities of skilled testers allow them to uncover complex vulnerabilities that automated scans miss entirely.
A good report includes proof of exploit, clear risk context, and prioritised remediation guidance-not just a list of theoretical issues.
Real-World Example: How Small Vulnerabilities Chain Together
To illustrate how penetration testing works in practice, consider this scenario we uncovered during a recent web application assessment. What looked like two minor, low-severity issues turned into a complete compromise of administrative access.
The application had a stored cross-site scripting vulnerability-a common flaw where user input isn't properly sanitised. On its own, this might seem manageable. But when we combined it with an open URL redirect elsewhere in the application, the impact escalated dramatically.
Here's how the attack chain unfolded:
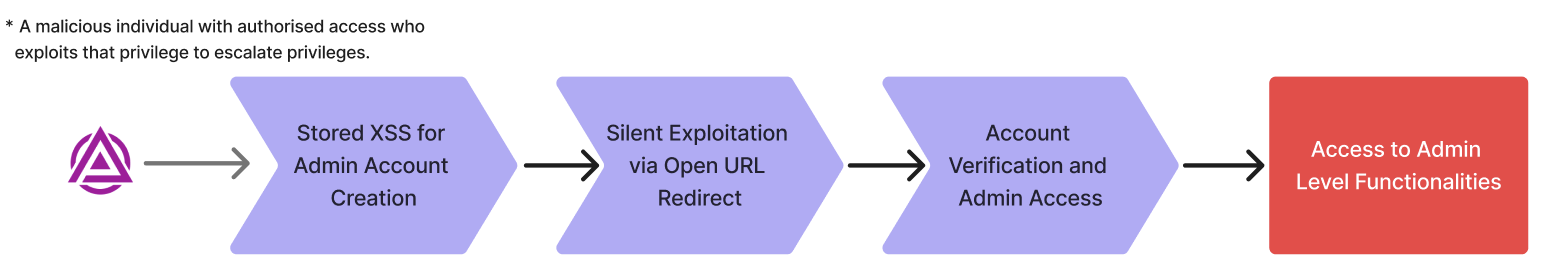
A standard user account (the kind any customer might have) was used to inject a malicious payload through the stored XSS vulnerability. The payload was crafted to create a new administrator account, but it needed to execute when viewed by someone with existing admin privileges.
This is where the open URL redirect came in. By crafting a legitimate-looking link, we could direct an administrator to a page containing the injected payload-without raising suspicion. When the admin visited the compromised page during normal application use, the script executed silently in their browser, sending a privileged API request to create a new admin account with credentials we controlled.
The administrator never saw anything unusual. No error messages. No warnings. Meanwhile, a new admin account now existed in the system, fully controlled by the attacker.
Through this privilege escalation attack chain, a low-privilege user moved from standard customer access to full administrative control-silently manipulating the system without alerting the legitimate admin. Neither vulnerability alone would have achieved this. Together, they created a critical business risk.
This is exactly why penetration testing matters. Automated scanners might flag each vulnerability individually as moderate risk. A skilled tester sees how they connect-and demonstrates what an attacker could actually do with them.
Why Your Business Needs Web Penetration Testing
Every business that operates online-whether you sell products, provide services, or simply have a customer portal-faces the same fundamental risk: your web application is accessible to anyone with an internet connection, including people who want to exploit it.
The Financial Reality
Data breaches are expensive. The Verizon 2024 Data Breach Investigations Report found that basic web application attacks-exploiting common vulnerabilities like SQL injection and cross-site scripting-were responsible for 12% of all confirmed breaches in 2025, an increase from the previous year. When you add credential theft and other application-layer attacks, web applications feature in roughly a quarter of all breaches.
These aren't abstract statistics. A breach means immediate incident response costs, regulatory fines, legal fees, customer notification expenses, and the long tail of reputational damage that follows. In the UK alone, the average cost now exceeds £3.29 million per incident.
Compliance Requirements
Many regulatory frameworks now mandate or strongly recommend regular penetration testing. If your business handles payment card data, PCI DSS Requirement 11.4 requires it. Healthcare organisations must consider it under HIPAA. Financial services firms face requirements under various regulations. ISO 27001 certification expects it as part of a mature security programme.
Penetration testing isn't just about avoiding breaches-it's increasingly about demonstrating due diligence to regulators, auditors, and business partners.
Customer Trust
Your customers trust you with their data. A breach doesn't just cost money-it costs relationships. When customers learn their personal information was exposed because of a preventable vulnerability, that trust is difficult to rebuild. Proactive security testing demonstrates that you take their data seriously.
When Your Business Needs a Web Penetration Test
A product launch heads to production on Friday. It touches payments and customer data. Do you ship, or do you pause for a focused test?
Timing matters. Here are the common triggers that signal when to schedule a web application penetration test:
- Before major releases that introduce new authentication flows, payment paths, or sensitive data processing.
- After significant changes such as a framework upgrade, cloud migration, new API gateway, or identity provider switch.
- Following an incident or near miss. Validate that root causes are removed and no side doors remain.
- Third-party integrations including payment processors, analytics SDKs, and customer SSO connections.
- Compliance or customer requirements (such as PCI DSS) that call for periodic testing with evidence of remediation.
- Mergers and acquisitions where inherited web properties carry unknown risk.
How Often Is Enough?
Testing frequency depends on your exposure and rate of change:
High-risk, high-change applications (customer portals, payment systems): Test at least annually, plus after major changes.
Moderate-risk applications (internal portals with some sensitive data): Test every 12 to 18 months or after significant updates.
Low-risk applications (static or informational): Light testing every 18 to 24 months plus continuous scanning.
Consider business cycles too. If holiday traffic, annual enrollment, or quarterly releases create peak load, schedule testing early enough to fix findings without pressure.
Don't forget the long tail: staging environments, admin consoles, old subdomains, and forgotten APIs are often overlooked but can be just as vulnerable. An attack surface-led approach pulls these into scope.
What Gets Tested in a Web Penetration Test
A comprehensive web penetration test examines your application from multiple angles, looking for weaknesses that attackers commonly exploit. The OWASP Top 10 provides a useful reference for the most critical web application security risks.
Authentication and access controls: Can someone bypass your login systems? Could a regular user access administrator functions? Are password reset processes secure?
Input handling: What happens when someone submits unexpected data through forms, search boxes, or URLs? Could malicious input allow attackers to access your database or execute commands on your server?
Session management: Are user sessions properly protected? Could an attacker hijack a legitimate user's session and act on their behalf?
Business logic: Beyond technical vulnerabilities, testers look for flaws in how your application handles business processes. Could someone manipulate prices, bypass payment flows, or access data they shouldn't see?
Configuration and infrastructure: Is your web server properly configured? Are unnecessary services exposed? Is sensitive information leaking through error messages or hidden files?
Understanding Your Attack Surface
Not all parts of your web application carry equal risk. A login page accessible to anyone on the internet presents different challenges than an internal administration panel used by two people in your organisation.
This is where an attack surface-led approach becomes valuable. Rather than treating penetration testing as a tick-box exercise, this methodology starts by understanding what matters most to your business: What keeps you up at night? What would an attacker actually want? What's the objective?
We favour an assumed breach mindset. That means we test what happens if an attacker slips past the first control, then measure how well you contain, detect, and recover. It's a realistic way to judge resilience.
The attack surface pyramid provides a framework for thinking about this systematically:
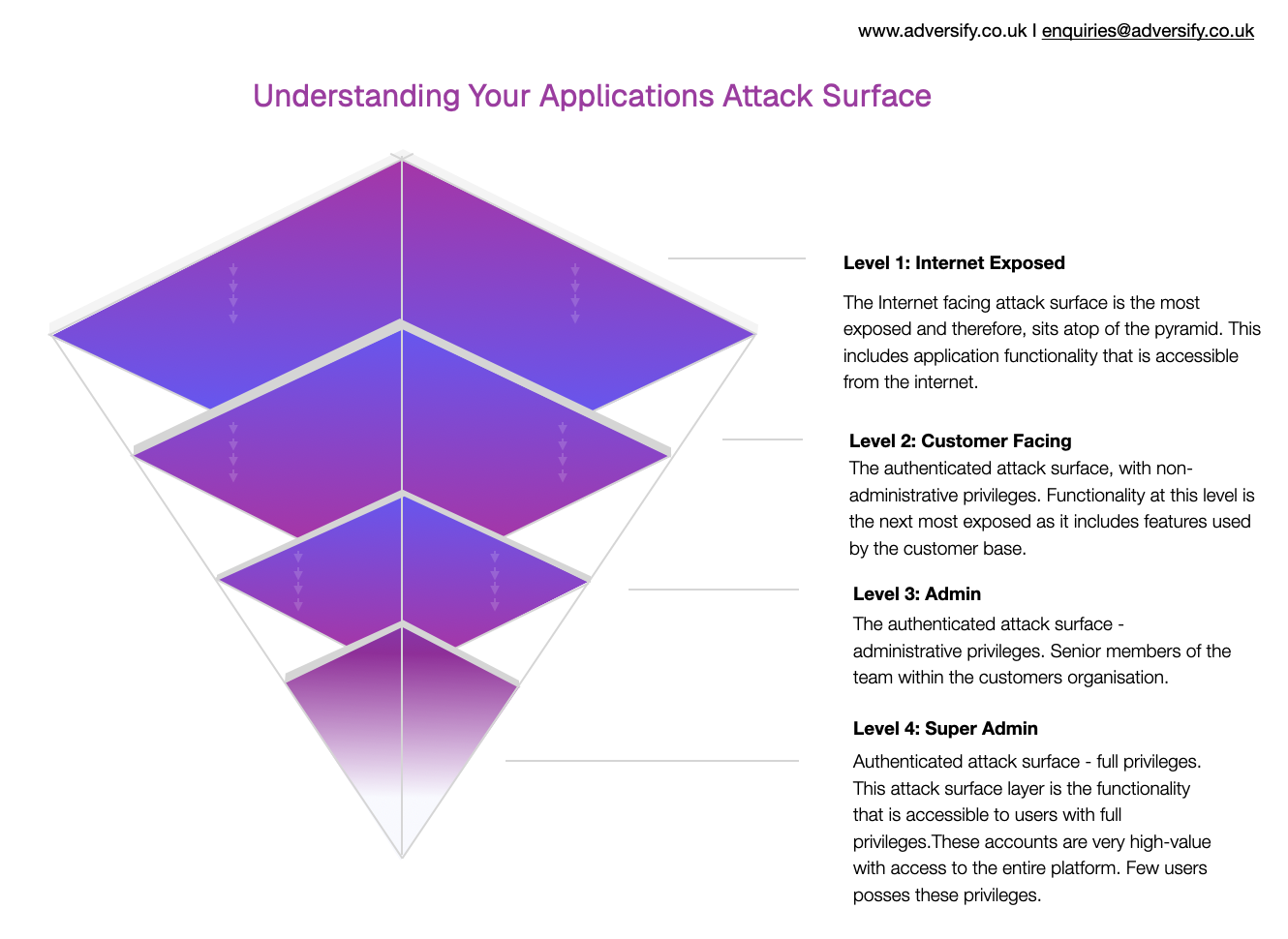
Level 1: Internet Exposed - The most exposed layer, sitting at the top of the pyramid. This includes functionality accessible to anyone on the internet: registration forms, login pages, search features, and public booking systems. Anonymous users can access these features, making them the most likely entry point for attackers.
Level 2: Customer Facing - The authenticated attack surface with non-administrative privileges. This covers features your customer base uses after logging in: personal account management, individual features, and read-only permissions in business platforms. Exposed to your entire user base, this layer is the next priority.
Level 3: Admin - The authenticated attack surface with administrative privileges. Senior team members access these features: team management settings, write/modify permissions, and role-specific management interfaces. Fewer people have access, but the impact of compromise is higher.
Level 4: Super Admin - The highest-privilege layer. Full platform access with complete control. Very few users possess these privileges, but these accounts are extremely high-value targets. A compromise here affects everything.
This framework allows you to prioritise testing based on actual risk exposure. You don't necessarily need a full-blown penetration test of every layer immediately-you can focus your budget on your biggest attack surface first, then expand coverage as resources allow.
Beyond Traditional Penetration Testing
While traditional penetration testing provides valuable baseline coverage, an attack surface-led methodology takes it further by incorporating the entire attack surface within scope. This provides holistic coverage that aligns more closely with how real-world attackers operate.
Real attackers don't limit themselves to predefined technology silos. They look for whatever weakness gets them to their objective. By thinking the same way-understanding why someone would want to attack your organisation and what they're after-penetration testing becomes a genuine simulation of real threats rather than a compliance exercise.
This approach ensures that no critical exposure is overlooked simply because it falls outside a traditional scope definition. The result: more actionable, relevant, and risk-prioritised findings.
What to Expect: The Testing Process
Understanding what happens during a penetration test removes uncertainty and helps you prepare properly.
- Scoping and objectives: We define objectives and tailor the testing approach using our attack surface-led methodology, ensuring scope and strategy align with real-world threats and your business priorities.
- Reconnaissance: Testers gather information about your application the same way an attacker would-identifying technologies, mapping functionality, and understanding how the system works.
- Testing and exploitation: Using a combination of manual techniques and specialised tools, testers probe for vulnerabilities and attempt to exploit them. When weaknesses are found, they demonstrate the real-world impact.
- Reporting: You receive a clear report detailing what was found, how serious each issue is, and exactly how to fix it. Good reports explain technical findings in business terms so you can prioritise effectively.
- Remediation support: Questions arise during fixes. We remain available to clarify findings and verify that remediation was successful.
Read more about the Web Application Service we offer and methodology here: Web Application Penetration Testing
Frequently Asked Questions
Will penetration testing break my website?
Professional penetration testers take care to avoid disruption. Testing is typically conducted against staging or pre-production environments where possible, and testers communicate closely with your team throughout. The goal is to find weaknesses, not to cause downtime.
How long does a web penetration test take?
Duration depends on the size and complexity of your application and how many attack surface layers are in scope. A focused test of internet-exposed functionality might take a few days. A comprehensive test covering all privilege levels takes longer. We'll provide a clear timeline during scoping.
What's the difference between a vulnerability scan and a penetration test?
Vulnerability scanners are automated tools that check for known issues. They're useful for regular hygiene but produce false positives and miss complex vulnerabilities. Penetration testing uses human expertise to find weaknesses that scanners miss, chain vulnerabilities together, and demonstrate real-world impact. Think of scanning as a health questionnaire; penetration testing is the full medical examination.
How often should we conduct penetration testing?
At minimum, annually-and after any significant changes to your application. Many organisations test more frequently, especially those in regulated industries or with rapidly evolving applications. Continuous monitoring and regular testing together provide the best coverage.
Do we need to test everything at once?
No. An attack surface-led approach allows you to prioritise based on risk and budget. You might start with your most exposed internet-facing functionality, then expand to authenticated features and administrative interfaces in subsequent tests. This makes penetration testing accessible regardless of budget constraints.
What qualifies someone to perform a penetration test?
Look for testers who follow industry-recognised methodologies (like OWASP and NIST), hold relevant certifications (such as OSCP, CREST, or CHECK), and can demonstrate experience testing applications similar to yours. Independence is also important-testers should be separate from those who built or manage the systems being tested.
Take the First Step
Every web application has vulnerabilities. The question is whether you find them first or wait for someone else to.
If you're ready to understand where your web application's weak points are-and what it would take to address them-book a call to discuss the best approach for your situation. We'll help you define objectives, identify your most critical attack surfaces, and tailor a testing approach that aligns with real-world threats and your business priorities.
Contact us at enquiries@adversify.co.uk or visit www.adversify.co.uk to book your call.
Offensive security articles from the front line
Security is who we are
Founded in 2022, Adversify is a specialist penetration testing consultancy. We redefine penetration testing engagements and help businesses discover attack paths and vulnerabilities, commonly exploited by real-world adversaries.
Our attack surface-led approach ensures comprehensive coverage of the environment.


Explore our Services
Browse our comprehensive suite of offensive security services designed to fortify your organisation's defenses against potential cyber threats. Our offerings are tailored to identify vulnerabilities and enhance your security.



